Cybersecurity is paramount in ensuring the safety and integrity of applications, systems, and networks. Penetration testing, often called pen testing, is a crucial component of this process.
It involves skilled assessors simulating real-world attacks to identify vulnerabilities and methods malicious actors could exploit to compromise security measures.
In this article, we will explore the top five methodologies for penetration testing services and how they contribute to the overall security posture of an organization.
Organizations employ various methodologies to perform penetration testing. These methodologies are structured approaches to identify and address application, system, or network vulnerabilities.
While the core principles remain the same, different methods may use varied terminologies for the phases involved. The typical steps found in most pen test methodologies are:
- Pre-engagement Steps
- Intelligence Gathering
- Threat Modeling
- Scanning and Enumeration
- Exploitation
- Post-Exploitation
- Reporting
Now let us explore the top five methodologies for penetration testing and how they contribute to the overall security posture of an organization.
-
The Open-Source Security Testing Methodology Manual (OSSTMM)
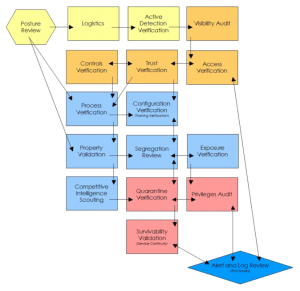
The Open-Source Security Testing Methodology Manual (OSSTMM) is a comprehensive and flexible security testing methodology that addresses various aspects of information security.
It is maintained by the Institute for Security and Open Methodologies (ISECOM) and consists of five channels: Human Security, Physical Security, Wireless Security, Telecommunications Security, and Data Networks Security.
Each channel focuses on security and provides testing guidelines for vulnerabilities and threats.
The OSSTMM is a valuable resource for organizations of all sizes, offering comprehensive coverage, peer-reviewed credibility, flexibility, risk identification, mitigation, and overall improvement of security defenses.
-
The Open Web Application Security Project (OWASP)
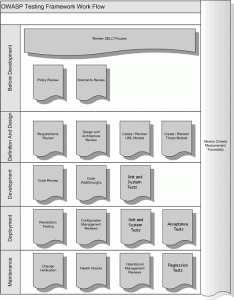
The Open Web Application Security Project (OWASP) is a leading non-profit organization that offers expertise, resources, and training to assist organizations in enhancing the security of their web applications.
The Open Web Application Security Project (OWASP) is a recognized industry security standard. It provides a comprehensive framework and guidelines for addressing security issues in web applications.
OWASP offers a range of resources, including documentation, tools, and best practices, to help organizations effectively identify, mitigate, and prevent vulnerabilities in their web applications.
With its extensive community support and continuous updates, OWASP is crucial in promoting secure development practices and ensuring the integrity and protection of web applications across various industries.
3. The National Institute of Standards and Technology (NIST) Guidelines
The National Institute of Standards and Technology (NIST) is a U.S. government agency leading measurement, standards, and technology.
They develop and publish guidelines for information security, including NIST Special Publication 800-115, a comprehensive guide for penetration testing.
This manual covers all aspects of the testing process, from planning to reporting, offering advice on tool selection, and effective communication with stakeholders.
NIST 800-115 is a valuable resource for organizations seeking to enhance their security through penetration testing, providing authoritative guidance to identify and address security risks.
Its benefits include being a comprehensive, reputable, and accessible guide tailored to an organization’s specific needs, improving security, and lowering the chances of a breach.
4. The Penetration Testing Execution Standard (PTES)
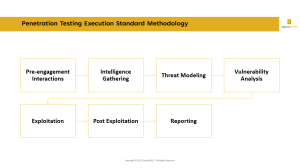
The Penetration Testing Execution Standard (PTES) is a community-driven standard created by security professionals to enhance the value and quality of penetration tests.
It outlines a seven-phase methodology, including pre-engagement, intelligence gathering, vulnerability analysis, exploitation, post-exploitation, reporting, and remediation.
PTES is a comprehensive and authoritative resource for organizations seeking to improve their security posture by identifying and addressing security risks through penetration testing.
Its benefits include its comprehensive coverage, maintenance by experienced professionals, customization options, and potential to mitigate security risks and enhance overall security.
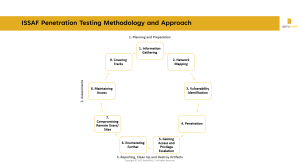
5. The Information Systems Security Assessment Framework (ISSAF)
The Information Systems Security Assessment Framework (ISSAF) is a community-driven methodology developed by security professionals to enhance the quality and value of penetration testing.
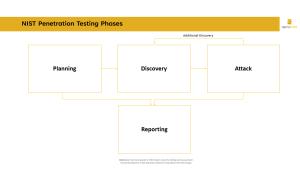
ISSAF defines five key phases: planning, discovery, vulnerability assessment, exploitation, and reporting. This comprehensive guide helps organizations improve their security posture by identifying and mitigating vulnerabilities.
A reputable organization maintains ISSAF, offers customization options, and is free to use. By following ISSAF, organizations can strengthen their security measures, reduce the risk of security breaches, and benefit from a widely respected standard in penetration testing.
Conclusion
Effective penetration quality assurance testing services and is crucial in today’s increasingly interconnected and vulnerable digital landscape.
An organization can comprehensively evaluate its security measures by employing a suitable methodology. Each methodology brings unique perspectives and insights, enabling businesses to identify and address vulnerabilities proactively.
By utilizing these methodologies, organizations can identify vulnerabilities, mitigate risks, and strengthen their overall security posture.
These methodologies offer comprehensive coverage, authoritative guidance, customization options, and community support, enabling organizations to safeguard their digital assets and mitigate security threats proactively.