More than sixty percent of the world’s population uses the internet. It’s such common knowledge that doubting whether we are doing it correctly is almost trivial.
Below the surface level of scrolling TikTok, there’s more to the internet than meets the eye.
Unfortunately, the internet is not just fun and games.
There are a lot of security and anonymity threats the common user is unaware of.
Concealing your identity and bypassing various restrictions is essential to get the most out of the internet with minimal risk. That’s exactly what proxies are for.
How Does the Internet Work?
The basics are all familiar you go to a website and then type in a URL after which a site appears on the screen.
It is even easier on a smartphone because many popular services have apps.
But what’s happening behind the curtains helps us understand why we must be careful.
Commonly, the internet functions as a network of networks. Computers may be linked to a device to transmit and receive information. It could represent your network at home in which your computer, phone TV and others are linked to the router. Additionally, this network is able to communicate with different networks, which form the Internet as we have it.
They can share data by sending data packets.
We can think of them as data units that travel in and between networks. They are used to identify devices (handshake), request data (HTTP request), and receive it (HTTP).
The traveling of such data packets creates an uninterrupted internet connection between those who are requesting data (clients) and those who are providing it (servers).
Such travel is bound by rules that all devices must abide by or else they won’t participate in the network.
The internet protocol defines these sets of rules. For our purposes here, the most important rule is that every device must be identified by an IP address.
It is a combination of alphanumeric characters that serves as a distinctive identifier for each device within a particular network.
When a client subscribes to an internet service provider (ISP), they are assigned a verified IP address specific to their location.
One device will receive a public IP address. If that device is a router, it can assign private IP addresses for each other device that uses this network to connect to the internet.
Not guarding your IP address creates a host of security threats and usage limitations.
The Three Most Common Internet Threats
Showing your IP address is like displaying your ID document to everyone you meet. The most immediate threat is losing your privacy.
By knowing your IP address, websites can log when you have entered when you leave, and what pages you visit.
Since the IP is tied to a location, it’s easy to make an online profile of you. If websites are sharing data, it’s even easier.
Even worse for privacy is that your ISP or network administrator can also see everything you do online.
The websites also must identify themselves, and it isn’t so difficult to trace.
The second risk is that both your ISP and websites can limit the data that is accessible to you on the internet.
For example, it’s common for e-commerce websites to keep higher prices for customers from certain locations.
They can identify visitor locations from the IP addresses, so it’s easy to target regions that can pay more.
The government or other actors can influence the ISPs to block certain websites by their IPs.
It is a strong restriction of citizen liberties, most commonly used by authoritarian countries to prevent uprisings and limit information.
The most dangerous threat can be a Distributed DDoS (DDoS) attack. When you engage in the case of DDoS attacks, cybercriminals try to interfere with a server’s connections by flooding it with an overflowing amount of requests.
Each network has a limit to limit the amount of requests it can handle. If an attacker is adept in their attack, they could exceed the limit and send more requests than the servers can cope with, eventually causing the server to be shut down.
Although DDoS attacks typically are associated with servers on websites, however, they also can attack private networks. One of the best ways to mitigate the threat is to conceal an IP address.
What Do Proxies Change?
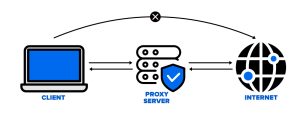
Proxies are intermediary servers that stand in between you and the dangers of the internet.
With a proxy, you do not send the data packets with requests yourself. The proxy does it for you.
You provide a request to a proxy, and it sends it on your behalf.
For example, if you acquire a proxy server in the Philippines, you will first send your requests there, and they will reach the target server only indirectly.
As such, the website’s server does not see your IP address, only the proxy servers in the Philippines.
Proxy Types
Datacenter proxies are the fastest proxy type. They are set up in servers of data centers and use high-speed commercial internet access to bring optimal speed results.
However, data centers are not used by common internet folk, so it is relatively easy for websites to block or restrict such IPs that are created virtually on servers.
Residential proxies are a type that fixes the legitimacy issues.
It uses home devices and connections, which makes it more difficult for websites to detect and block residential proxy users.
The price of blending is speed, as these residential connections are significantly slower than those of data center proxies.
It depends on your task on which of the proxy types will perform better, but both are usually paid.
Proxy infrastructure is quite costly to providers, but some quality ones do provide trials or an occasional free proxy list that allows you to test how a certain proxy will perform.
Conclusion
Setting up such proxy servers doesn’t have to be costly and slow your connection speed. If you know your tasks and choose the proxy server type correctly, you can navigate the internet both safely and securely.