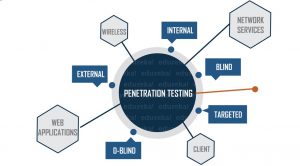
In today’s world, you need a solid network security protocol more than ever before. With so much sensitive information being transmitted online, it is essential to make sure that your data is protected.
You’ve probably heard of network security penetration testing but aren’t quite sure what it is. Don’t worry, you’re not alone! This procedure entails creating an imitation attack on your network in order to expose any flaws that may exist.
In this blog article, we’ll respond to the inquiry “what is network security penetration testing?” and why it’s so essential for companies today. We’ll also take a look at who needs it the most and least and discuss some of the features that make a good network security penetration test. Finally, we’ll present you with some of the greatest tools for performing a network security penetration test. Let’s get this party started, shall we?
Basics Of Network Security Penetration Testing
It is the process of simulating an attack on a network in order to find any vulnerabilities that may exist. Internal and external networks may both be tested in this manner. The aim is to discover any flaws in the system that might be exploited by a hacker.
Once these weaknesses are found, they can then be fixed before an actual attack takes place. This is a smart notion since it helps to guarantee the protection and privacy of your information.
It is important to note that network penetration testing should only be carried out by experienced professionals. This is because it can be a complex process and there is a risk of causing damage to the system if it is not done correctly. You may always start looking online for top pentesting companies if your internal team has no expertise in executing a pentest.
Reasons For Network Security Penetration Testing
There are many reasons why you may need to carry out network security penetration testing. The most popular reason is to inspect the system for any flaws, in order to prevent an attack.
This form of the test may also be utilized to assess the efficacy of your security measures. It can help you to find any weaknesses in your system and make sure that they are fixed before they can be exploited.
Security penetration testing is also frequently employed for compliance reasons. In order to guarantee the data’s safety, many sectors have their own rules that must be followed.
Penetration testing can help you to meet these requirements by ensuring that your system is secure. Finally, network penetration testing can also be used for research purposes.
It can help you to understand how hackers operate and what methods they use to attack systems. This information can then be used to improve the security of your network.
Who Needs Network Security Penetration Testing?
Network security pen-testing is relevant for any business that relies on a network to operate. Small and large businesses alike are affected.
If you store any sensitive data on your network, it is especially important to ensure that it is secure. This type of testing can help you to find any vulnerabilities in your system so that they can be fixed before an attack takes place.
It’s also worth noting that network security penetration testing is not only for major corporations. If you are responsible for the security of a public or private network, you may also need to carry out this type of testing.
The Drawbacks
One of the most significant disadvantages is that it can be a complex process and there is a risk of causing damage to the system if it is not done correctly.
This means that it should only be carried out by experienced professionals. Another disadvantage is that it can be time-consuming, especially if you need to carry out a black box test.
Finally, network penetration testing may not be effective if you do not have full knowledge of the system. This is because a white box test may be required to find all of the vulnerabilities in the system.
The Alternatives To Network Security Penetration Testing
There are some alternative solutions to network security penetration testing. A vulnerability scanner is an alternative.
These scanners can help you to identify any vulnerabilities in your system and make sure that they are fixed before an attack takes place. However, they cannot provide the same level of detail as a penetration test.
Another alternative is to use a honeypot. This is a decoy system that is designed to attract hackers and distract them from your real network.
Honeypots can be effective at deterring attacks but they cannot provide the same level of information as a penetration test.
Finally, you could use a firewall. This will help to protect your network from attacks but it will not be able to identify any vulnerabilities in your system.
What Do Network Security Penetration Testing Tools Look Like?
Some of the most popular options include:
- Nmap
- Astra’s Pentest
- Metasploit
- Wireshark
- Burp Suite
This is only a sample of the equipment that may be utilized for network security penetration testing. There are numerous alternatives to choose from, so it’s critical to get the appropriate tool for the task.
Conclusion
Network security penetration testing is a process that is designed to assess the security of a system. It can be utilized to identify any flaws in the system, allowing them to be addressed. The most suitable tool for your system will be determined by the size and complexity of your needs.
Author Bio-
Ankit Pahuja is the Marketing Lead & Evangelist at Astra Security. Ever since his adulthood (literally, he was 20 years old), he began finding vulnerabilities in websites & network infrastructures. Starting his professional career as a software engineer at one of the unicorns enables him in bringing “engineering in marketing” to reality. Working actively in the cybersecurity space for more than 2 years makes him the perfect T-shaped marketing professional. Ankit is an avid speaker in the security space and has delivered various talks in top companies, early-age startups, and online events.