KrnlKeyPhp: Krnl Key It is a mix of numbers and letters, and anywhere between 30 and 32 characters. It’s a crucial component of the executor, without which you can’t inject or execute the scripts.
It’s not at all possible to link the kernel into Roblox without an appropriate key.

Understanding Cryptographic Keys: KrnlKeyPhp
Keys for cryptographic encryption come in a variety of types, including keys that are private and public as well as symmetric keys and hash functions.
These keys are crucial in securing online communications and ensuring data stays private and secure throughout transmission.
Importance of KrnlKeyPhp in Web Development
Web developers are now recognizing that it is important to integrate Krnl Key PHP in their software.
In doing this they enhance the security of their applications by securing them against attacks and access by unauthorized persons to user information that is sensitive.
How KrnlKeyPhp Works

On a technical basis, Krnl Key PHP operates to provide a secure platform to manage and generate keys.
It allows the incorporation of cryptographic keys with web-based applications. It provides an easy process of encryption as well as decryption.
It ensures that information remains protected and safe against possible cyber-attacks.
Benefits of Using KrnlKeyPhp
Utilizing the Krnl Key PHP brings forth several advantages to web developers.
Improved security options, protection against unauthorized access, and powerful encryption features for data are among the main benefits that help to create a secure online experience.
Common Challenges and Solutions
However, even the most experienced users may face difficulties when installing the Krnl key PHP.
This could be anything from issues with key storage to the complexity of key rotation.
There are solutions and software developers can navigate these issues with the right instructions and top methods.
Best Practices for Implementing KrnlKeyPhp
To ensure optimal performance and the proper functioning of KrnlKeyPhp, developers need to follow the most effective guidelines for key management.
Updates regularly secure storage protocols and efficient key rotation methods are vital to maintain the security of your system.
Similarity to other Key Management Systems
Within the extensive field of key management tools, Krnl Key PHP stands out.
Comparing it to similar programs will provide developers with insight on its distinctive characteristics and benefits, which allows them to make informed choices concerning their security systems.
Case Studies
Actual examples demonstrate the success of the application of the Key PHP Krnl. Studying case studies reveals the benefits and learnings from organizations that are embracing this management tool.
Future Trends in Cryptographic Key Management
Technology advances and also does the area of the management of cryptographic keys.
Analyzing the latest trends in cryptography provides the developers a peek of what is to come, which allows them to keep ahead in the security of their apps.
Security Considerations for Developers
The role of developers is crucial in the protection of key cryptographic encryption.
This article offers advice regarding safeguarding keys, keeping current on security protocols and staying vigilant to new security threats.
User Feedback and Reviews
Perspectives of those who have tried Krnl Key PHP offer valuable perspectives.
The discussion of common problems and the highlights of the positive aspects of their experiences will help potential users to make educated decisions when incorporating the tool in their web design projects.
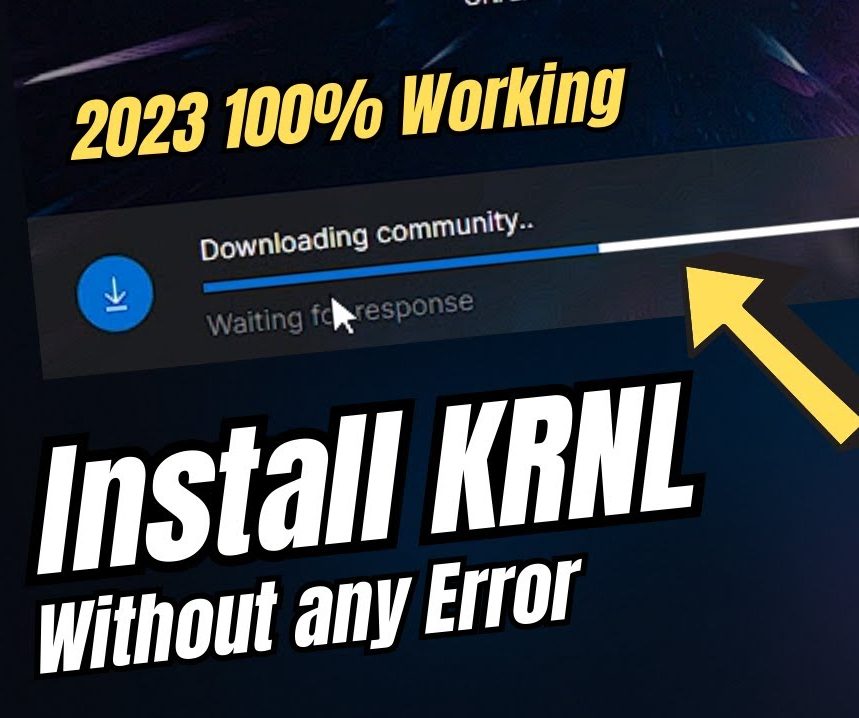
How to Install Krnl & Generate KrnlKeyPhp?

- The first step is to disable the firewalls for Windows or Antivirus and then download the Krnl installation.
- The main reason to disable the Antivirus software is that it does not consider programs such as Krnl in the category of malware.
- Open the Roblox storefront and play any game you like.
- Then, you can launch the exploit software and then complete the kernel key system in order to create the key for Linkvertise.
If the above link not working copy the below URL and paste in a new tab:
https://cdn.krnl.place/getkey.php
or
https://cdn.krnl.place/getkey
- When you receive you have the Krnl Key, enter it into the Ky box, then select submit.
- While you’re at it take a moment to download the script the script you prefer.
- Finally, the script executor appears in the display and will have the Inject button on the right. It is possible to execute the script of your preference.
What is Krnl Key Bypass?
Krnl comes with a range of levels that are compatible with particular versions of the gaming engine Roblox.
Each week, you’ll be receiving updates for Roblox’s gaming engine. This means that exploits such as Krnl must be constantly changing their injector and executer configuration.
If the two systems aren’t optimized properly they could cause a number of problems.
Then, you must make the Krnl key in case these updates have not been automatically applied.
Krnl Key refers to a type of text or sequence of characters that is entered by the user into the Krnl key system to be able to utilize the exploiting resources.
But, the Krnl key may not be compatible with certain devices or require a lengthy duration. You can however get around the Krnl key, and do so without installing another program.
To bypass your Krnl Key system access the Linkvertise site and choose an option called Krnl Key bypass choice that matches the system’s description.
Then, select the free access option and a brand new page will open. Then, all you need to do is need to complete a quick job and proceed with the process of creating keys. It is also possible to watch the Youtube video on each Krnl key bypass tutorial.
Conclusion
To conclude, Krnl Key PHP emerges as a formidable ally within the field of managing cryptographic keys.
The seamless integration of it into websites provides web developers with an effective solution to secure the data they store and also ensures a safe user experience online.
You may be interested
Google Home Review : Speaker Quality, Functions, Price Best Deals
Google Home Review : Home speaker quality, what does google...
Android O (Oreo) Review : Advantages | Disadvantages | Problems | Pros and Cons
Android o (Oreo) Review : Advantages | Disadvantages | Pros...
Apps to Track Text Messages
Text messages are the oldest technological form of typed communication...