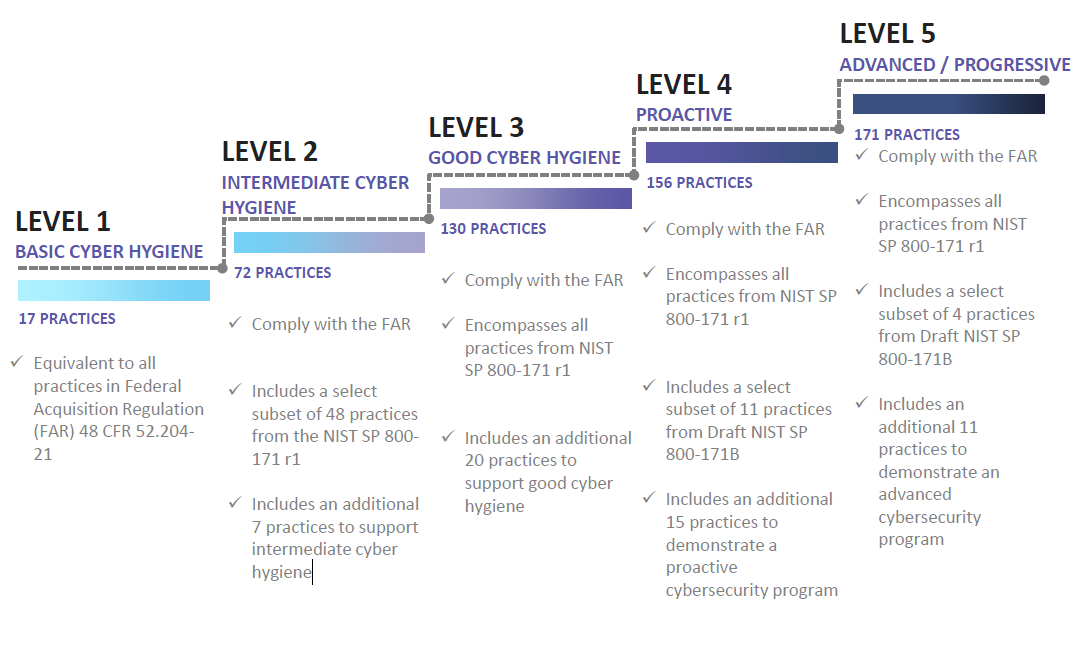
With the globe becoming more digital, the security of information that is sensitive has become the top priority for businesses. One type of such data includes Controlled Unclassified Information (CUI).
In this piece, I’ll walk you through the most important systems and network configurations needed to secure CUI.
CUI refers to information that is sensitive and that is not classified however must be secured because of its possible impact on privacy, security of the nation, or any other significant interest.
It could include information related to law enforcement, defense export controls, defense, and much more. Knowing and controlling CUI is crucial to guarantee that you comply, and also to avoid unauthorized access or divulgation.
Understanding the Importance of System and Network Configuration for CUI
To effectively safeguard CUI for your business, you need to be aware of the configurations for the network and system. The configuration of a system is the setting and settings of the individual PC systems.
Network configuration refers to the establishment and management of the interconnected network infrastructure. Both play an important role in protecting against CUI and minimizing the risks.
The proper system configuration includes implementing security measures, including encryption, access control, and log-logging systems.
Network configuration, on the contrary, concentrates on the establishment of secure communications channels and segregating sensitive information installing firewalls, as well as security systems for detecting intrusions.
What is CUI System Configuration?
CUI configuration of the system is the following practices and rules specifically designed to secure CUI on individual computer systems. It includes setting up operating systems, software as well as databases to protect the security, confidentiality, and accessibility of CUI.
The most important aspect of CUI system configuration is control of access. It involves the creation of user accounts, setting roles and rights, as well as setting up a strong password policy.
In addition, encryption is a crucial aspect of CUI configuration. By encrypting sensitive information, you can ensure that, even in the event of being obtained or used by unauthorized users, the data remains inaccessible and inaccessible.
Utilizing encryption techniques that are strong along with secure key-management techniques businesses can secure CUI from disclosure by unauthorized parties.
What is the Purpose of the ISOO CUI Registry?
The Information Security Oversight Office (ISOO) maintains all the documents that constitute CUI.
The goal of maintaining the CUI registry of the ISOO CUI registry is to offer the same definitions and obligations in the field of CUI to every government entity that may be in touch with it, as well as contractors who collaborate alongside CUI.
Except for a handful of exceptions, CUI follows the exact guidelines.
Key Elements of Network Configuration for CUI
Configuring the network to support CUI concentrates on the creation of the most secure and robust network that allows for the transfer of sensitive data without exposing the user to breach of data due to unauthorized access.
In the first place, network segmentation is essential. When dividing the network into distinct zones or segments organizations can limit the vulnerability of CUI to potential hackers.
That means, that even if there is a breach in just only one area, the damage is contained and prevents unauthorized access to the other zones.
They act as a buffer between the network’s internal and threats from outside, observing the flow of traffic in and out for compliance with security rules.
IDS On the other on the other hand monitors the network’s activity and notifies administrators about any suspicious or suspicious behavior.
Finally, secure remote access is vital to organizations that require employees to connect to CUI via remote locations. Virtual Private Networks (VPNs) offer a safe and secure link between users from remote locations and an enterprise’s network.
They ensure the security of sensitive data regardless of whether it is accessed from outside the security perimeter.
Compliance Requirements for CUI System and Network Configuration
These regulations outline the required actions and procedures that have to be in place to secure CUI and to ensure that they comply with all applicable legislation and rules.
Furthermore, companies that collaborate in conjunction with organizations that work for the U.S. Department of Defense (DoD) have to comply with Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204-7012.
This law obliges contractors to establish particular security measures, such as the configuration of networks and systems for the protection of CUI.
In understanding and adhering to these requirements for compliance companies can be sure that the configurations of their network and system comply with standards of best practice and industry guidelines, thereby protecting CUI from access by unauthorized persons or information disclosure.
Who is in Charge of CUI information?
The National Archives and Records Administration (NARA) serves as the Executive Agent (EA) for Controlled Unclassified Information (CUI) and possesses the authority to oversee information security policies across all federal government domains.
Different types of employees are involved in classified information systems and critical nonclassified information systems. the NARA is the ultimate authority to oversee federal agencies.
CUI is also labeled using the ability to control dissemination. They include:
- NOFORN: No Foreign Dissemination
- FED ONLY: Federal Employees Only
- FEDCON: Federal Employees and Contractors Only
- NOCO There is no distribution to contractors
- DL ONLY: Dissemination list controlled
- REL to REL TO: Authorized to release only to certain nationals (Ex: REL TO USA)
- PLAY ONLY The disclosure is permitted to an international recipient the provision of an original copy
- Attorney-client Protection by privilege for attorneys.
- Lawyer Work Product The distribution of this product is prohibited unless authorized in advance by an attorney overseeing.
Why is DoD Instruction 5200.48 Important?
DoD Instruction 5200.48 is the formal base of the entire DoD instructions on protecting CUI.
It defines the fundamental structure for the CUI program as well as the major government departments that companies should be conscious of for reporting as well as monitoring reasons.
The book also provides the fundamental goals and duties of CUI security, including the rules and guidelines for following the rules.
A key rule to follow is that businesses must label CUI at specific locations by using symbols or language to identify the type of information is it and who has access to it as well as which authorities are in charge of its oversight.
It is the responsibility of organizations to make sure that they are clear about their markings and that dissemination and access are managed according to the guidelines.
Which document contains DoD cyber rules regarding CUI along with CTI?
DoD Instruction 5200.48 explains what Controlled Unclassified Information is. The DFARS 252.204-7012 encourages protecting Covered Defense Information and reporting cyber incidents.
Contractors must include this clause in subcontracts involving such information or critical support operations.
The two clauses protect from unauthorized disclosure of confidential information.
Security Best Practices for CUI via Systems and Network Configuration
Secure CUI via network and system configurations requires the use of the best practices in the industry. They are intended to limit vulnerabilities, strengthen security safeguards, and shield CUI from threats.
- Use the Concept of Least Privilege: This means granting users the privileges they need for their work and to access CUI.
- Always Patch and Upgrade Software and Systems to fix the vulnerabilities that are known and to safeguard against exploits that could be able to occur.
- Set up robust monitoring and logging methods to identify and react to any attempts at access that are not authorized or suspicious activities.
- Perform regular security assessments, vulnerability tests, and penetration tests to find the weaknesses and then address them. the configuration of your network or system.
- Inform employees about security awareness and best practices to handle CUI Emphasizing the significance of integrity, confidentiality, and accessibility.
If you follow these guidelines organizations can boost their network configurations and systems to reduce the chance of accessing CUI and ensure conformance with regulations.
Tools and Technologies for CUI System and Network Configuration
Effective network and system configurations to support CUI usually call for the use of specific devices and techniques. They automate and simplify the configuration process, making sure of uniformity and lessening the risk of human errors. Below are a few commonly used software tools to configure the CUI Network and system configuration.
- System for Configuration Management: These software tools aid in the management and automation of the configuration of systems, making sure that systems are all configured effectively and safely.
- Intrusion Detection Systems: IDS monitors networks and alerts administrators of suspicious or illegal activities, assisting in identifying and addressing potential threats.
- Security Scanning Tools for Vulnerability: They search for and analyze systems and networks for security holes, giving organizations important information to patch or protect their systems and configurations.
- Tools for encryption: These tools assist in protecting sensitive information through the conversion of it to the inaccessible ciphertext to ensure that it remains secure even if it’s the data is accessed by someone else.
Through the use of these technologies and tools companies can speed up the configuration process, increase security measures, and safeguard CUI better.\
Challenges and Common Pitfalls in CUI System and Network Configuration
When implementing network and system configurations to support CUI is essential but it’s not without some challenges as well as potential dangers. C Below are some of the most common issues and mistakes to avoid with regards to CUI the configuration of networks and systems:
- A Lack of Awareness and Education: In many organizations, there is a lack of needed information and comprehension of CUI systems and network design best practices. This leads to inadequate security of confidential data.
- The Complexity of Compliance Requirements: The requirements for compliance can be complicated and can be difficult to understand and apply, resulting in possible gaps in the networks and system configurations.
- Human Error: Mistakes in configuration or oversights could be the result as a result of human error which can lead to vulnerabilities or security risks.
- A Rapidly Changing Threat Landscape: Cyber-attacks are always changing, which makes it difficult to stay up-to-date with the most recent security tools and techniques.
To tackle these problems To overcome these challenges, companies need to invest in quality courses of education and training, constantly review and improve their networks and systems configurations as well as stay up-to-date with current security trends as well as the best techniques.
Training and Certification for CUI System and Network Configuration
To ensure that the networks and system configurations to support CUI can be effectively used companies should consider investing in the training and certification of their employees. They provide people with the expertise and skills to protect CUI and keep it in compliance.
Many training companies offer classes and certificates that are specifically focused on CUI networking and system configuration.
The courses cover subjects like access control security, encryption, network segmentation, and compliance needs. Through these accreditations, they can show their skills and commitment to safeguarding CUI.
Conclusion:
Understanding and applying the correct networking and system configurations is crucial to protecting Controlled Unclassified Information (CUI). In compliance with the requirements of compliance by following good practices as well as utilizing appropriate technology and tools, companies can efficiently protect CUI from unauthorized access or divulging.
The investment in education and certification programs can further increase the skills of those in charge of CUI networking and system configuration. By staying informed of new security trends and continually updating the configurations organizations can adjust to changing threats and guarantee the continuous safety of CUI.
Be aware that the security of CUI isn’t a once-in-a-lifetime job, but a continuous commitment. When prioritizing network and system configurations, companies can build strong defenses against risks and remain in compliance of regulations. Begin implementing these techniques today to discover the mysteries of CUI and protect your private personal information.