Whether you think you are a low-risk or high-risk internet user, cybersecurity should be a significant part of your security plans. You could easily have your identity stolen and used for illegal purposes or your money spent by cyber attackers. A company could lose its credibility if it is hacked and customer information stolen from their computers.
Bear in mind that these attackers are continuously trying to get into your company or personal accounts. Since people tend to use the same password for several accounts, it is easy for attackers to use credential stuffing to gain access.
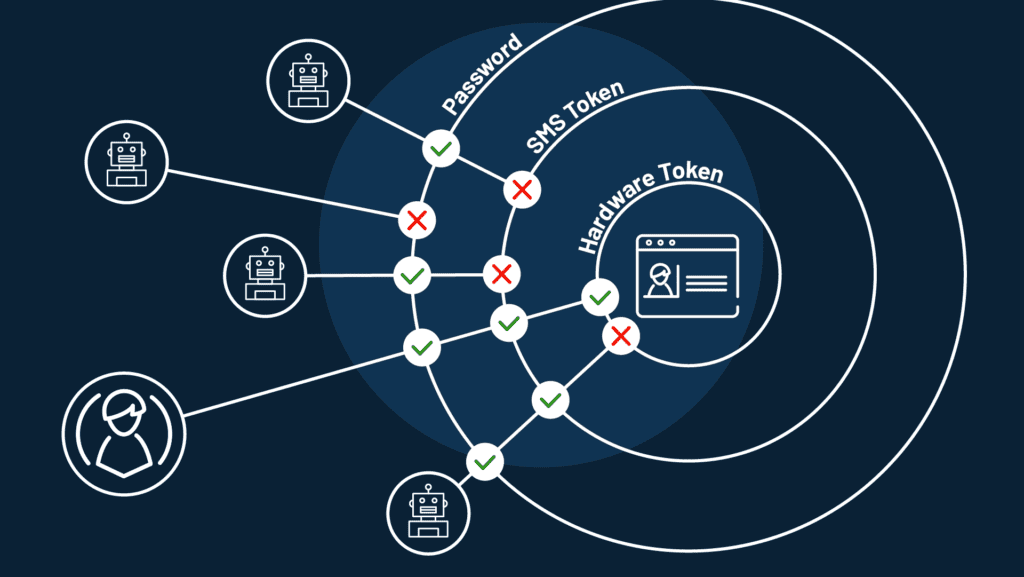
Credential stuffing refers to the automated use of pre-collected account information to log into various user accounts. This information can be bought on the dark web or stolen during a data breach on a company. Since people use the same password on different accounts, attackers use the stolen information on various sites.
When they gain access, they can get valuable personal information such as credit card information and engage in identity theft. They may also take over the account and register for gaming accounts and buy expensive virtual items.
Bear in mind that credential stuffing is different from brute force attacks. Brute force attacks involve the use of large amounts of computing power to try to gain access using common password combinations.
Attackers using credential stuffing already have real login details and are not guessing. Credential stuffing requires that an attacker enters the login details manually, but that can take a very long time. That is why they use a bot that can do the same thing faster than a human being.
5 Effective Ways to Prevent Credential Stuffing
Here are five ways you can prevent credential stuffing.
Use Unique Passwords

Credential stuffing benefits from the tendency of most people to use the same password for several online services. Since credential stuffing involves trying to log into a large number of services using each of the stolen logins, they are bound to find a way into your social media accounts, online shopping, and other services that you use.
Those will give them access to information they can use, such as your credit card. They can then steal your identity, and in some cases, empty your bank account. People use the same password because they do not want to forget their password. It is possible to use different passwords and not forget any of them.
Even without technology, you can create an infinite number of passwords using a personal encryption rule. Ensuring that you do not use personal information like your date of birth as a password is an excellent way to start. You could also use a service like LastPass to generate and store strong passwords for each of your online services.
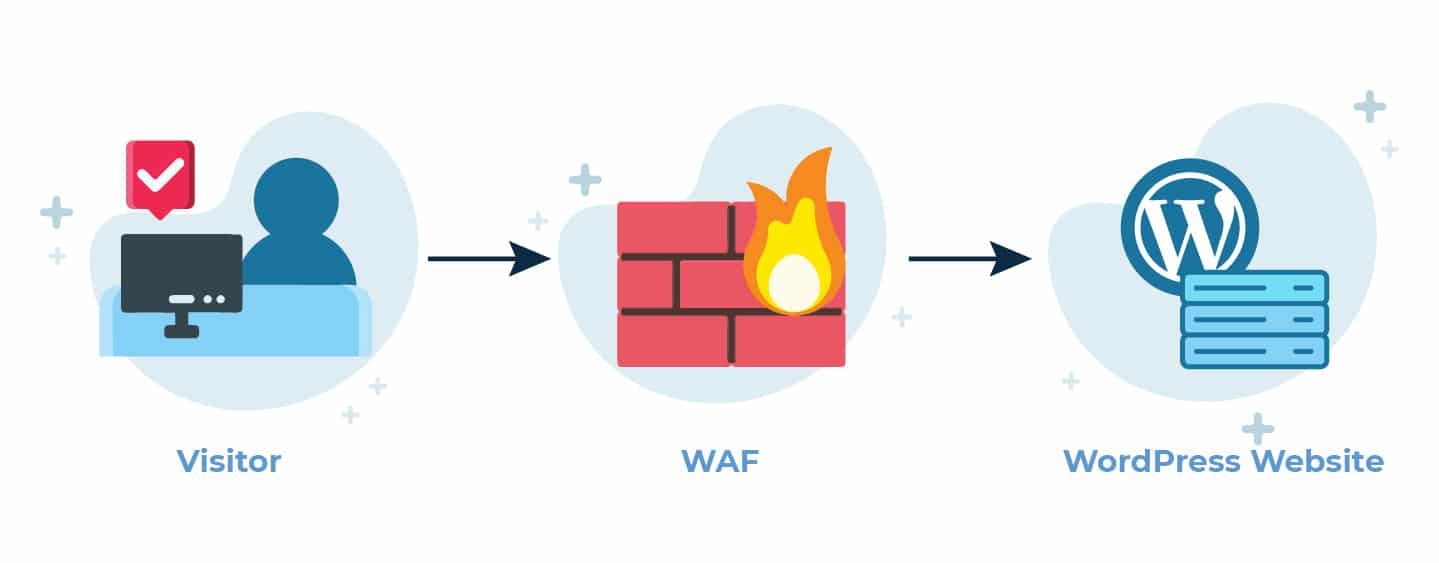
Use a Web Application Firewall
Your service provider should have a good web application firewall that can detect suspicious activity from botnets. Web Application Firewalls are not made to prevent credential stuffing, but they can find suspicious login attempts, such as when many logins occur at once. Hosting companies can make use of WAFs to prevent data breaches as a result of web attacks.
Limit Authentication Requests And Set Up Alerts

Any service provider should restrict the number of failed authentication requests. Think about it, without an authentication limit an attacker can attempt an infinite number of times to log in. That means bots can keep trying the collected information until they find one that works for your account.
Failed attempts can be limited based on IP addresses, devices, locations, or timeframes. Using one of these may not be sufficient to protect your account, but all of them may offer some level of protection. Banks and other financial institutions restrict failed login attempts to 3 or 4, the device or IP address notwithstanding.
If you reach the limit they freeze the account, and you will need to visit a branch to get it reactivated. That may be extreme for other services, but the service provider should limit attempts to 3 in every hour to reduce the attack speed. It is also essential that they send users emails to alert them about these attempts. When you receive such an email, improve the security of your account by changing the password.
Multi-factor Authentication
2-factor authentication or multi-factor authentication requires that users provide more than one piece of information before accessing the account. That way, even if an attacker has your login information, they will still not access your account. This information comes in three types.
- Knowledge-based Multi-factor Authentication
In this case, customers must provide the answer to a pre-selected question. The question is usually about their personal life, such as a mother’s maiden name or a childhood best friend. This method is the weakest because attackers can easily obtain this type of information.
- Possession-based Multi-factor Authentication
In this case, users will receive a one-time-only password via text message, which gives them access to the account. Several financial institutions use this for their customers. It ensures that people who do not have access to your cell phone, such as cyber attackers, cannot log into your account.
- Biometric-based Multi-Factor Authentication
Biometric authentication involves the use of facial recognition or thumbprint readers. Many devices have fingerprint readers and facial recognition cameras that customers can use after they enter their password. The downside is that few people have these devices, and therefore service providers can not make this a mandatory requirement.
Screen for leaked Credentials

Service providers can use screening solutions to check their user credentials against a database of compromised credentials. They can use the information published on the dark web to create this database. Service providers must inform users of compromised accounts to change their passwords.
That said, this only works for data published publicly and will not help if it was sold privately. End-users can use a service like Havebeenpawned.com to check whether accounts associated with their email addresses have been compromised.
Your security online is as essential as your security offline. Make sure that you take the necessary steps to protect yourself and your clients from cyber attacks.