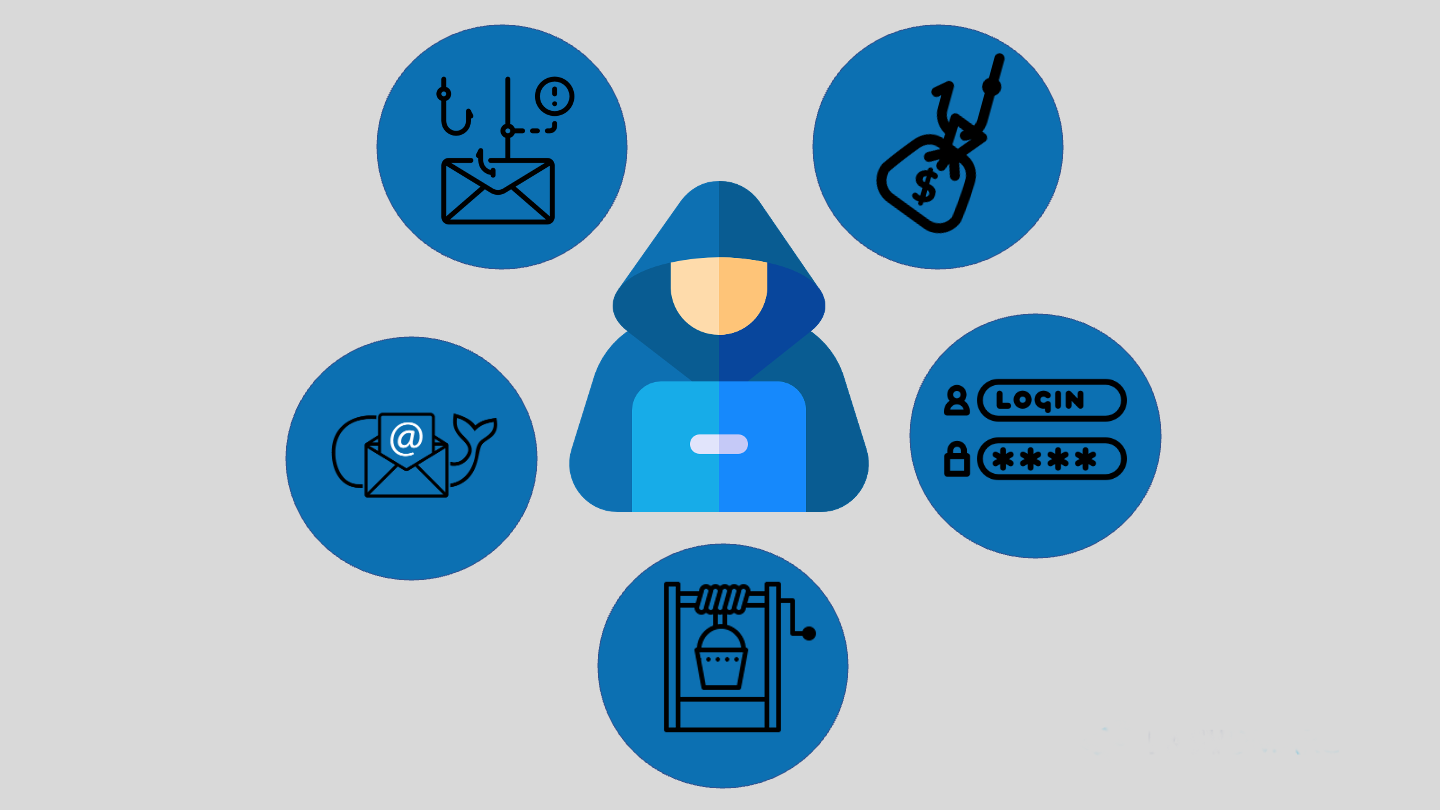
In terms of cybersecurity, a social engineering attack tries to manipulate your emotions to trick you.
A hacker may use greed, fear, anger, sadness, or lust to deceive you into sharing your confidential data, visiting a fraudulent website, or downloading malicious software.
Social engineering attacks are becoming so compelling that even the most experienced Internet users are falling for them.
In a state of panic, it’s easy to share your credit card information online with what you believe is a genuine entity to avoid trouble.
Unfortunately, once you realize that you’re the victim of a social engineering attack, it’s too late.
Here are some tips that can help you stop social engineering attacks:
Take a Breath
The first step is to take a breath. Take time to think before reacting.
Do I really need to visit this website?
Do I really need to download this file?
Do I have to share this information?
The more time you take to think before you act, the less likely you are to fall prey to a social engineering attack.
Keep in mind that hackers don’t want to give you time to think. They use social engineering to cloud your judgment.
Recognize Red Flags
It’s critical to recognize red flags in order to defeat social engineering.
- Grammatical errors: Watch out for spelling or grammatical mistakes, whether it’s an email, website, or pop-up window. Legitimate organizations pride themselves on their language. They usually try to avoid errors at all costs.
- Design errors: Just like language, organizations take pride in their design. Whether you’re on a website or reading an email, look for images that look out of place or are of low quality.
- Alarmist language: Is the communication forcing you to act urgently to avoid a computer virus, take advantage of a shopping deal, or avoid tax fraud? Hackers usually employ alarmist language in social engineering attacks.
- Uncharacteristic communication: Official emails will never ask for your usernames, passwords, or credit card data. They won’t carry links that look like gibberish. Immediately report phishing emails to the right source for investigation.
Verify, Verify, and Verify
Imagine that you’re working when you receive an email with an attachment from the IT department.
The email suggests you immediately open the file for new cybersecurity software. But when you look closer, something doesn’t seem quite right.
The file seems too small to be a cybersecurity program, while the email address doesn’t match that of the company.
To avoid such spear-phishing attacks, please verify anything suspicious, whether it’s an email from your retailer, bank, or someone in your organization.
Please also be wary of new online friends who behave suspiciously. They could be hackers running a con.
Use Top Cybersecurity Tools
Despite your best efforts, you may be deceived by a social engineering attack. It can happen.
Please download good anti-malware software to protect yourself from malicious software.
You should also frequently use a Trojan scanner to keep your system clean because Trojan virus attacks rely on social engineering to infect users.
Malware that uses social engineering to infect computers exploits software weaknesses to breach security and privacy.
In addition to good downloading cybersecurity software, always use the newest security updates to plug holes and stay safe.